VMware Transit Connect is a pivotal feature within VMware Cloud on AWS (VMC), designed to revolutionize how organizations establish high-speed and resilient connections between their Software Defined Data Centers (SDDCs) in VMC and a multitude of other resources. This globally available capability, now generally available across all VMC commercial regions, leverages SDDC Groups to simplify the management and interconnection of your cloud resources.
At its core, VMware Transit Connect, facilitated by SDDC Groups, enables you to effortlessly define collections of SDDCs, Native AWS Virtual Private Clouds (VPCs), and on-premises environments that require seamless interconnection. Beyond simplifying multi-SDDC management, SDDC Groups also streamline security policy implementation within individual SDDCs. Powering this simplified experience is the VMware Managed AWS Transit Gateway (VTGW), a fully managed service by VMware that provides the robust underlying connectivity fabric.
The initial VMware Transit Connect service offering focuses on three primary connectivity models, addressing the most common hybrid cloud networking needs:
- SDDC to SDDC Connectivity: Establish direct, high-bandwidth links between your VMware Cloud on AWS SDDCs.
- SDDC to Native AWS VPC Connectivity: Integrate your SDDCs with your existing Native AWS VPCs for seamless hybrid applications.
- SDDC to On-premises Connectivity over Direct Connect Gateway: Extend your VMC SDDC to your on-premises infrastructure via AWS Direct Connect.
These connectivity models are designed to address the most prevalent customer requirements and will continue to evolve based on user feedback and the ongoing partnership between VMware and AWS, ensuring VMware Transit Connect remains at the forefront of hybrid cloud networking solutions. Let’s delve deeper into the specifics of each connectivity model and understand how they operate.
Before implementing VMware Transit Connect, it’s crucial to understand the prerequisites:
- SDDCs must be running on VMC release 1.11 or later to support Transit Connect features.
- For SDDCs and VPCs to be part of an SDDC group, they must reside within the same AWS region for optimal performance and latency.
- Ensure that SDDC management CIDR blocks do not overlap to avoid routing conflicts and maintain network integrity.
- While overlapping SDDC networks are technically possible, it’s important to note that overlapping segments will not be advertised across Transit Connect, potentially leading to connectivity issues.
Understanding traffic flow is also key to leveraging VMware Transit Connect effectively. A fundamental rule is that any communication flow must involve at least one endpoint within a SDDC managed by VMware Transit Connect. This requirement ensures observability and simplifies troubleshooting, as VMware support teams can monitor at least one side of the connection. The service architecture incorporates distinct routing domains: the Member routing domain for SDDC communication with other SDDCs, VPCs, or on-premises, and the External routing domain, which exclusively routes traffic to member SDDCs. This translates into the following permitted and prohibited traffic patterns:
- SDDC to SDDC: Permitted – Enabling direct communication between VMC SDDCs.
- SDDC to VPC: Permitted – Facilitating hybrid applications spanning SDDCs and Native AWS VPCs.
- SDDC to On-premises: Permitted – Extending your VMC environment to your physical data center.
- VPC to VPC: Prohibited – Direct VPC to VPC communication is not supported through Transit Connect.
- On-premises to VPC: Prohibited – On-premises to VPC communication is not directly supported through Transit Connect.
With these considerations in mind, let’s explore the network topologies you can build with VMware Transit Connect.
Network Topology 1 – SDDC to SDDC Connectivity
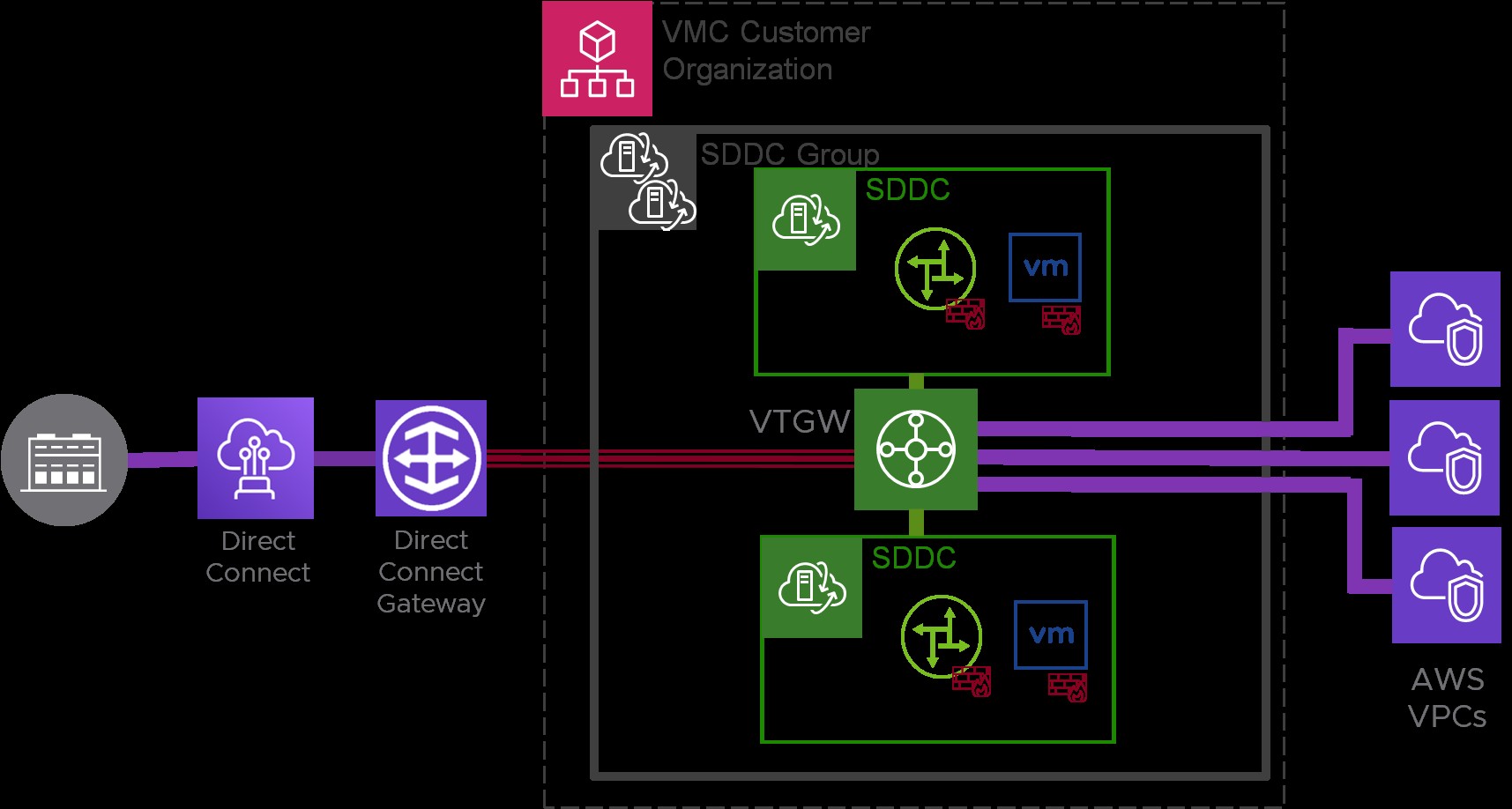
The SDDC to SDDC topology, illustrated in Figure 2, allows you to connect multiple VMware Cloud on AWS SDDCs within the same AWS region, creating a highly interconnected cloud environment.
In this example, three SDDCs are deployed in the same AWS region. Two of these SDDCs are configured as members of an SDDC Group, enabling them to communicate directly via the high-speed VPC attachment established by the VTGW.
Setting up this SDDC to SDDC connectivity begins in the VMware Cloud on AWS Console. Navigate to the Actions menu and select “Create SDDC Group”.
This initiates a straightforward three-step process. First, you’ll name your Transit Gateway and provide a description. Next, select the SDDCs you wish to include in the group. Finally, acknowledge the terms and conditions before clicking “Create Group.”
Once “Create Group” is selected, the automated backend processes begin, provisioning the necessary components and establishing connectivity. Initially, the SDDCs in the group will display a “Connectivity Status” of “PENDING” in the view details page. Upon completion of these background tasks, the status will automatically update to “CONNECTED,” indicating successful establishment of VMware Transit Connect.
To verify the configuration, navigate to the “Routing” tab. Here, you can review the network prefixes learned from each SDDC participating in the SDDC Group, ensuring proper route propagation.
For deeper insights within each SDDC, a dedicated “Transit Connect” tab is now available in the left navigation menu. This provides SDDC-specific routing information and status related to VMware Transit Connect.
With the underlying network connectivity established between SDDCs through VMware Transit Connect, the next crucial step is configuring security policies. VMware’s security-first approach means that default firewall policies will initially prevent communication between resources in different SDDCs, even after establishing Transit Connect. To enable traffic flow, appropriate gateway firewall rules must be explicitly defined.
This is where the SDDC Group construct provides further administrative simplification. The SDDC Group automatically maintains a dynamic list of networks advertised by each member SDDC, VPC, and on-premises connection. It then intelligently populates system-managed groups that can be directly utilized in your NSX Distributed Firewall policies.
These system-managed groups, reflecting the SDDC Group membership, can be used as source and destination objects within your firewall rules, dramatically simplifying policy creation. While these groups offer a streamlined approach, you retain the flexibility to create more granular and explicit firewall rules if needed. The example below illustrates the use of SDDC Group Firewall Policy objects. Note the “Applied To” field, specifically selecting the “Direct Connect Interface.” This is important because the VPC attachment between the SDDC and the VTGW traverses an NSX Edge router interface named “Direct Connect Interface,” requiring firewall rules to be applied to this interface for effective enforcement.
By configuring these firewall policies, you complete the process, achieving end-to-end communication between your VMware Cloud on AWS SDDCs leveraging the power of VMware Transit Connect.
Network Topology 2 – SDDC to VPC Connectivity
VMware Transit Connect significantly enhances hybrid cloud capabilities by enabling seamless connectivity between resources residing in your VMware Cloud on AWS SDDCs and Native AWS VPCs. This model reduces the reliance on traditional VPNs for hybrid connectivity, offering a more performant and manageable solution. Figure 3 illustrates a typical SDDC to VPC topology enabled by VMware Transit Connect.
Expanding upon the SDDC to SDDC topology, Figure 3 demonstrates the integration of Native AWS VPCs into the VMware Transit Connect architecture. Configuring this SDDC to VPC connectivity necessitates collaboration and coordination between administrators managing both the Native AWS VPC environment and the VMware Cloud on AWS SDDCs. Specifically, the AWS account administrator will require the following permissions and information:
- Read/write permissions to the specific VPC(s) that will be connected to VMware Transit Connect.
- The AWS Account ID(s) where these VPCs are located.
- The VPC IDs and CIDR blocks of the VPCs intended for connection.
On the VMware Cloud on AWS side, the user performing these operations must have Cloud Admin privileges.
To initiate the VPC integration process within VMware Transit Connect, navigate to the “VPC Connectivity” tab in the VMC Console and click on “ADD AWS ACCOUNT.”
You will then be prompted to enter the AWS account number associated with the VPC(s) you intend to connect to VMware Transit Connect.
After adding the AWS account ID, the status in the VMC console will initially show as “ASSOCIATING.” To complete the account association, access the AWS Console using an account with the previously outlined permissions. Within the AWS Resource Access Manager, you will find a pending “Resource Share” notification.
Click on the “VMC-Group” resource share, review the details, and then “accept the share” and confirm. The AWS console will then indicate that the invitation has been accepted.
Following successful acceptance in the AWS console and a short synchronization period, the status in the VMware Cloud on AWS Console will transition from “ASSOCIATING” to “ASSOCIATED,” indicating successful AWS account linking.
With the AWS account successfully associated, the next step is performed within the AWS Console, under the VPC service. Navigate to the “Transit Gateways” section and select “Create Transit Gateway Attachment.” Here, select the VTGW (which represents your VMware Transit Connect), the specific VPCs, and the subnets within those VPCs that should participate in the Transit Connect service. Click “Create attachment” to initiate the process. The screenshot below illustrates this step within the AWS Console.
A confirmation window will appear, and the attachment process will begin. Initially, the AWS Console will display the attachment state as “pending acceptance.” To finalize the attachment, return to the VMware Cloud on AWS Console. In the “VPC Connectivity” tab, you will now see the VPC you just attached in the AWS Console listed with a “PENDING ACCEPTANCE” status. Highlight the VPC and click “ACCEPT.” The status will briefly change to “PENDING” before transitioning to “AVAILABLE.” This process may take up to 15 minutes, depending on AWS processing times.
Once the status becomes “AVAILABLE,” the underlying network connectivity between your SDDC and VPC is established through VMware Transit Connect. However, unlike SDDC to SDDC communication, a few additional routing and security configurations are necessary. First, update the VPC routing tables within the AWS Console. Add routes to direct traffic destined for your VMC connected networks towards the VTGW. This ensures that VPC resources know how to reach the SDDC networks via VMware Transit Connect. An example of this route table configuration is shown below.
Crucially, remember to configure the Security Groups associated with your EC2 instances within the VPCs. These Security Groups act as instance-level firewalls and must be configured to allow the desired traffic flows to and from your SDDC networks. Similarly, revisit and adjust your NSX Gateway Firewall policies within your VMware Cloud on AWS SDDC to permit traffic to and from the newly connected VPC networks. VMware Transit Connect provides the network plumbing, but AWS Security Groups and NSX Gateway Firewalls remain the essential security enforcement points in this hybrid architecture.
Network Topology 3 – SDDC to On-Premises Connectivity
The final connectivity model offered by VMware Transit Connect facilitates extending your VMware Cloud on AWS SDDC to your on-premises infrastructure. Historically, establishing this type of connectivity often involved provisioning AWS Direct Connect circuits between your data centers and the SDDC, typically utilizing private Virtual Interfaces (VIFs). VMware Transit Connect introduces a streamlined approach using a new type of VIF: the Transit VIF. A Transit VIF is specifically designed to terminate between an AWS Direct Connect Gateway and a Transit Gateway (TGW), which in this case is the VMware-managed VTGW. AWS Direct Connect Gateways are global constructs, unlike region-specific SDDCs and VPCs, offering greater flexibility in connectivity design.
To configure Direct Connect Gateway integration with VMware Transit Connect, navigate to the “Direct Connect Gateway” tab within the VMware Cloud on AWS Console and click “ADD ACCOUNT.”
Complete the required fields, paying particular attention to the “Allowed Prefixes.” It’s important to note that AWS Direct Connect Gateway supports advertising a maximum of 20 prefixes to your on-premises networks. Therefore, consider network summarization strategies to efficiently advertise your on-premises networks within this limit.
The VTGW will then initiate a request to associate with the specified Direct Connect Gateway owner. The status in the VMware Cloud on AWS Console will initially display as “REQUESTED.”
The owner of the Direct Connect Gateway must then accept the proposed TGW association within the AWS Console. Locate the pending association request and accept it, as shown in the following screenshot.
After accepting the association, you will be presented with the opportunity to accept the BGP proposal. Click “Accept proposal” to proceed, and the systems will process the requests. Note that this process may take up to 20 minutes to complete.
Similar to the SDDC to SDDC and SDDC to VPC connectivity models, establishing Direct Connect Gateway connectivity with VMware Transit Connect requires updating security policies to fully enable communication. A key difference with on-premises environments is the potential presence of physical firewalls within your data center. These physical firewalls may also require updates to their routing configurations and security policies to allow traffic to and from the VMware Transit Connect resources in your SDDC.
VMware Transit Connect represents the initial release of this powerful solution, offering significant capabilities to simplify and address the complexities of hybrid cloud computing. As the service evolves, expect further enhancements and features based on customer feedback and the ongoing VMware-AWS innovation partnership.
Additional Resources
VMware Cloud on AWS Release Notes – https://docs.vmware.com/en/VMware-Cloud-on-AWS/0/rn/vmc-on-aws-relnotes.html#wn07313029
VMware Cloud on AWS FAQ – https://cloud.vmware.com/vmc-aws/faq#networking-general
VMware Cloud on AWS Networking and Security Documentation – https://docs.vmware.com/en/VMware-Cloud-on-AWS/services/com.vmware.vmc-aws.networking-security/GUID-0CD747E8-143D-476C-BE17-7DB991B32D37.html